Welcome to your go-to guide for unlocking the secrets of SOC 2! Navigating cybersecurity? You've likely heard of it, but why should you care? Simply put, it is a must-have auditing standard for ensuring secure data management by your service providers. It's not just a buzzword; it's a baseline requirement, especially if you're looking at SaaS options. Whether you're an entrepreneur or a data-conscious individual, this blog covers the essentials of SOC 2—why it's crucial, its impact on your business, and how to excel in compliance.
What is SOC 2?
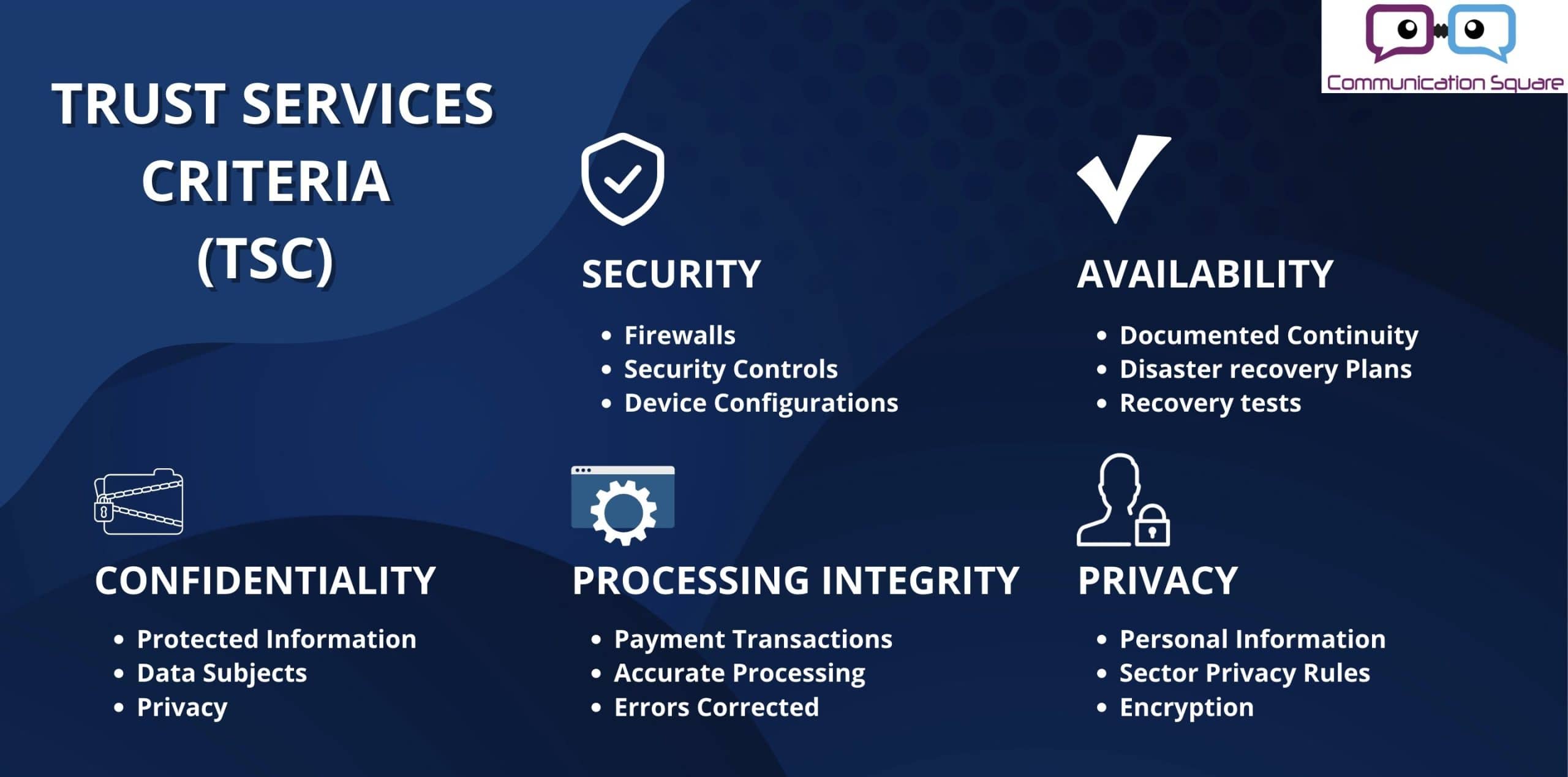
Service Organization Control 2 (SOC 2) is crafted by the experts at the American Institute of CPAs (AICPA), it serves as your ultimate roadmap for customer data management. It zeroes in on five crucial 'trust service principles'—security, availability, processing integrity, confidentiality, and privacy—to ensure you're not just storing data, but safeguarding it like a pro.
Think of SOC 2 as a business's 'seal of approval' for keeping your data safe and sound. Especially for companies that rely on Cloud storage rather than local storage and work with third-party vendors, having that SOC 2 badge is like saying, 'Hey, we’ve got your back!' So, in a nutshell, it isn't just a piece of paper; it's an industry standard that shouts credibility and trustworthiness. It's the reason clients can sleep better at night, knowing their data is in safe hands.
While SOC 2 is a crucial standard for many businesses, it's not the only SOC report that organizations might consider. SOC 1 is another important report that focuses on financial controls. To understand the differences between these two reports and determine which one might be more appropriate for your needs, you can refer to our detailed comparison of SOC 1 vs SOC 2.
Trust Services Criteria (TSC)
The Trust Services Criteria (TSC) are the pillars of SOC 2 compliance, encompassing five critical areas that ensure your organization's adherence to stringent compliance protocols. Understanding these criteria is vital for any organization pursuing SOC 2 certification, with Security being the cornerstone.
While Security is the fundamental pillar in the SOC 2 structure, the addition of other criteria — availability, confidentiality, privacy, or processing integrity — is optional. These are selected based on the specific services your company provides and the attributes you want to demonstrate and have scrutinized by auditors.
Before deciding which of these features to incorporate into your compliance structure, let's explore the 5 pillars of SOC 2 compliance trust services criteria, understanding how they can fortify your organization’s stance on governance and trustworthiness:
Security
The security criterion within the Trust Services Criteria is a required proof point, validating that your systems are safeguarded against unauthorized access and a spectrum of other risks. When clients of a service organization seek confidence about security and information protection, the security criteria come into play. This criterion is so comprehensive that its inclusion in an examination can, by itself, provide clients with the assurance they need regarding the safety of their data.
For example, as a cloud-based service provider undergoing an audit, expect a thorough evaluation of your access controls, encryption standards, and incident response procedures. This is to reinforce the defense mechanisms safeguarding customer data. It's essential to bear in mind that meeting the security criterion is not optional; it's a fundamental requirement for earning a SOC 2 attestation.
What is inside the Security Common Criteria?
The security criteria are often termed 'common criteria' due to their unique role in the Trust Services Criteria: they form a set of standards that are applicable across all five domains. In terms of SOC 2 criteria, security is referred to as protection of information and systems.
Protection of Information
This part of the security criteria is all about making sure that data is under lock and key at every stage—whether it's being gathered, created, used, processed, sent around, or stored. It's like ensuring that your valuables are safe not just at home but also when they're on the move.
Protection of Systems
Here, 'systems' cover any tech that handles electronic data—think of the digital workhorses that process, store, or transmit info vital to the services a company offers. The controls under scrutiny here are all about making sure there's a strong defense against and awareness of any chinks in the armor that could compromise security or processing.
The security Trust Services Criteria (TSC) also known as the common criteria, or the CC-series, comprises of nine distinct subcategories, each focusing on a specific area of security, ensuring that every angle of information and system protection is covered. Here’s an illustration of the CC-series:
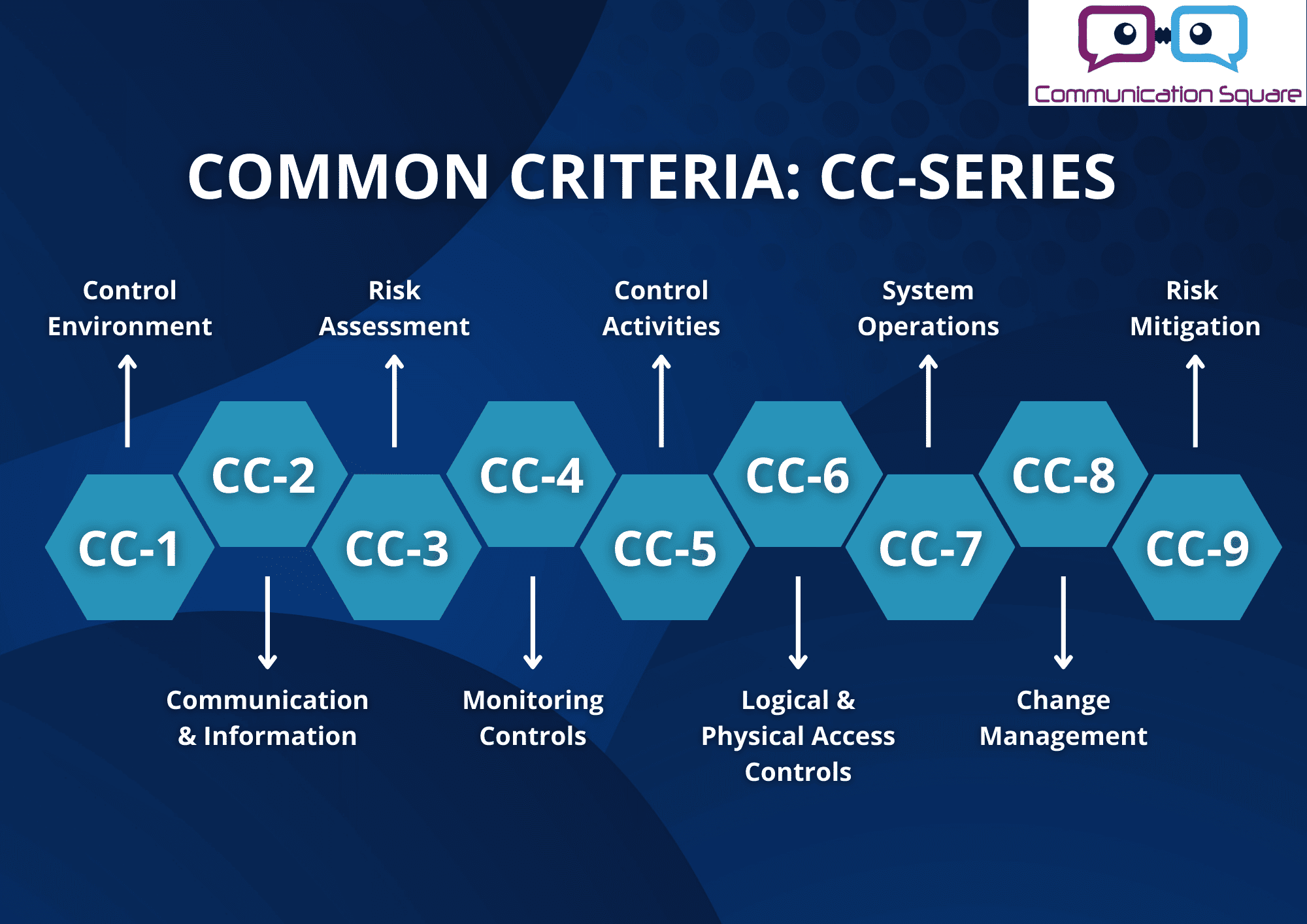
Here’s a tabular demonstration of what each cc-series' area of focus is:
CC-Series Area of Focus | Description |
|---|---|
CC1 - Control Environment | Does the organization value security and integrity? |
CC2 - Communication & Information | Are procedures and policies in place to ensure security? Do they communicate well to both internal and external partners? |
CC3 - Risk Assessment | Does the organization assess risk and monitor how changes impact that risk? |
CC4 - Monitoring Controls | Does the organization evaluate, communicate, and monitor the effectiveness of its controls? |
CC5 - Control Activities | Are the proper controls, technologies, and processes in place to reduce risk? |
CC6 - Logical & Physical Access Controls | Does the company implement data encryption? Does it regulate data access permissions and limit physical entry to server locations? |
CC7 - System Operations | Are systems monitored to ensure proper functioning? Are protocols ready for responding to incidents and managing disaster recovery. |
CC8 - Change Management | Are modifications to systems properly tested and approved beforehand? |
CC9 - Risk Mitigation | Does the company reduce risk by implementing appropriate business practices and managing its vendors effectively? |
Processing Integrity
The spotlight in this aspect of the trust services criteria is on the precision and thoroughness of data processing while safeguarding against data tampering or any potential inaccuracies due to fraud or mistakes.
Envision an IT company that manages a vast array of data transactions every day. Processing integrity within this context ensures that every bit of data, whether it’s a user command or a software update, is processed accurately. This means when a user performs an action or a system update occurs, the details are precisely recorded and processed, mirroring the user’s intention or the update requirements flawlessly.
To preserve this level of processing integrity, IT firms employ controls such as stringent code reviews, automated error checking, and continuous system monitoring, ensuring the integrity of data processing.
Availability
This aspect of the trust services criteria assesses the robustness of your disaster recovery tactics, the effectiveness of your system performance checks, and the resilience of your business continuity plans. It's all about reducing the amount of time critical systems are down and ensuring that services are accessible when needed.
Take, for example, an IT service provider that hosts cloud solutions; constant availability is essential. Particularly during peak business periods, it's vital that their infrastructure can manage unexpected surges in demand, ensuring clients have uninterrupted access to cloud services, maintain operational continuity, and, as a result, sustain a positive engagement with the service provider.
Confidentiality
Within the scope of the trust services criteria, there's a critical emphasis not just on security protocols, but also on demonstrating that sensitive information is managed responsibly from the moment it's collected until its disposal. Auditors zero in on the processes for identifying, safeguarding, and ultimately, securely disposing of confidential data.
For instance, in the world of IT and data management, confidentiality isn't just a good practice—it's imperative. This includes everything from proprietary code to customer data. Access to such sensitive information is carefully controlled with strong authentication systems.
Moreover, data encryption is standard practice to ensure information remains protected both in transit and when stored. Binding confidentiality agreements with staff and third-party partners is also crucial, bolstering the commitment to maintain strict confidentiality of the data entrusted to them.
Privacy
This trust services criteria component is all about protecting personally identifiable information (PII) using strategies like encryption, stringent access controls, and clear data retention policies.
Take a healthcare application, for example. It's essential to equip users with clear privacy policies and straightforward consent procedures. This empowers them to manage the use and distribution of their health data, ensuring they maintain control over their sensitive information.
Benefits of SOC 2 Compliance
Ready to level up your business? Let's talk about the benefits of SOC 2 compliance. This isn't just a fancy certificate to hang on your wall; it's your ticket to stronger client relationships, smoother business operations, and less stress around data security. Here’s why it is the business investment you didn't know you needed:

Who Needs SOC 2 Compliance?
The short answer is almost any business that deals with sensitive data, but let's break it down. SaaS companies practically consider it a rite of passage, while healthcare providers need it to assure the secure handling of patient data. Financial institutions and e-commerce platforms also benefit immensely given the sensitive nature of the transactions they handle.
Managed service providers also fall under this umbrella, as they're often the custodians of other companies' IT systems. Beyond individual business types, SOC 2 compliance is becoming a must-have due to evolving data privacy laws like GDPR and CCPA. It often shows up in contractual obligations and is a selling point in industry listings and business partnerships. In short, SOC 2 is quickly becoming more than a recommendation; it's setting the standard for data security across industries.
What is the Difference Between SOC 2 Type I and Type II?
Here are the two different types of SOC 2:
Type I: Reports evaluating a company's controls through SOC 2 is like taking a snapshot at a specific moment in time. It assesses whether the security measures in place are well-designed to protect data.
Type II: Reports evaluate the effectiveness of security controls over a typical span of 6-12 months, checking if they function as intended.
Here’s a tabular comparison of the differences between SOC 2 type I & II:
SOC Type I | SOC 2 Type II | |
|---|---|---|
Cost | Least expensive | Costly |
Duration to Attain | 3 - 6 Months | 6 - 12 Months |
What it does? | Short term solution to demonstrate compliance. | Long term solution to demonstrate compliance. |
Pros | Shorter audit windows, faster & less expensive | Longer audit window, more expensive |
Cons | May not provide enough assurance and may eventually need a type II | Provides a greater level of trust with clients and partners. |
Renewal | Every 12 Months | Every 12 Months |
Why is SOC 2 Important?
Think of it as the ultimate street card for your business. It's not just a shiny badge; it's a promise to your clients that their data is in safe hands. You know that icky feeling you get when handing over personal info to a sketchy website? A SOC 2 certification ensures your clients won't feel that way about your service. It’s also your golden ticket to landing clients in industries with tough data protection rules, like healthcare and finance.
Oh, and let's not forget about competition; flashing that SOC 2 badge can give you the edge in a crowded market. But it’s not just about showing off. It is also your personal cheat sheet to avoiding disastrous data breaches. Plus, if you're looking to reel in investors or high-profile partnerships, being SOC 2 compliant is like the cherry on top that makes you irresistible.
Conclusion
In a world where data breaches are becoming more frequent and costly, SOC 2 compliance isn't just a 'nice-to-have': it's a necessity. From SaaS providers to healthcare institutions, this certification is your badge of trust, signaling that you take data security seriously. It's a crucial factor that can set you apart in a crowded marketplace and make or break business partnerships. So, if you're not already SOC 2 compliant, now is the time to up your game.
Interested in taking your business's cybersecurity to the next level? Book a strategy call with us today. As a Microsoft Gold Partner, we offer top-notch security solutions tailored to your specific needs.
Last Updated 2 years ago ago
