Hey there! If you're like me, running a business in today’s fast-paced digital world, you know how crucial it is to keep your data and user identities safe. But let's be honest, figuring out the best ways to use Microsoft 365 Business Premium's security features can sometimes feel a bit overwhelming. That's exactly why I put together this guide on setting up Microsoft 365 identity protection—to simplify things and show you how to beef up your security without needing to be an IT guru.
As a business owner who's navigated these waters myself, and as a consultant who's helped others do the same, I understand the challenges you face. This guide will walk you through each step of setting up Microsoft 365 identity protection, from ensuring each team member has just the right access, to setting up fail-safes for emergencies, and making user authentication as painless as possible.
Follow along, and I'll help you secure your systems like a pro. Let’s make sure your business is as secure as it can be, so you can focus on what you do best—running your company!
Key Steps for Strengthening Microsoft 365 Identity Protection
Step 1: Apply Principles of Least Privilege
- Goal: Ensure each user has only the necessary permissions to perform their job.
- Actions:
- Identify Roles: Make a list of roles like 'Sales Manager', 'HR Coordinator', 'IT Support'. Determine what level of access each role needs. For example, IT Support needs admin access, whereas Sales Managers do not.
- Create Admin Accounts: For those needing admin access, create separate admin accounts. For example, if John is an IT Admin, create a secondary account named 'John-admin' for administrative tasks.
- Assign Roles: Go to Microsoft admin center > Users > Active users. Choose a user, select 'Manage roles', and assign them as ‘Global reader’ if they only need to view settings but not change them.
- Review Regularly: Every quarter, review access permissions to ensure they still align with job functions. Remove any excessive permissions identified.
Step 2: Create Emergency Access Accounts
- Goal: Set up backup accounts for system access in emergencies.
- Actions:
- Create Accounts: Create two new user accounts called 'backup-admin1' and 'backup-admin2'. These should have admin privileges but are used only in emergencies.
- Exclude from Policies: Ensure these accounts are exempt from Conditional Access policies that might restrict access.
- Secure & Monitor: Enable MFA on these accounts. Set up alerts to monitor any login attempts. These accounts should only be used when primary accounts are compromised.
Step 3: Set up Conditional Access
- Goal: Control who can access your system and under what conditions.
- Actions:
- Access Conditional Access: Navigate to Azure portal > Azure Active Directory > Security > Conditional Access.
- Create New Policy: Name your policy ‘Secure Office Access’. Apply it to user groups like 'All Employees'.
- Configure Conditions: Set a condition to require MFA from locations outside the office network. Example: If a login attempt is made from outside the IP range 192.168.1.1 to 192.168.1.255, require MFA. Learn more about Conditional Access.
- Enable Policy: Turn the policy on and monitor its effects. Adjust settings based on feedback and observed access patterns.
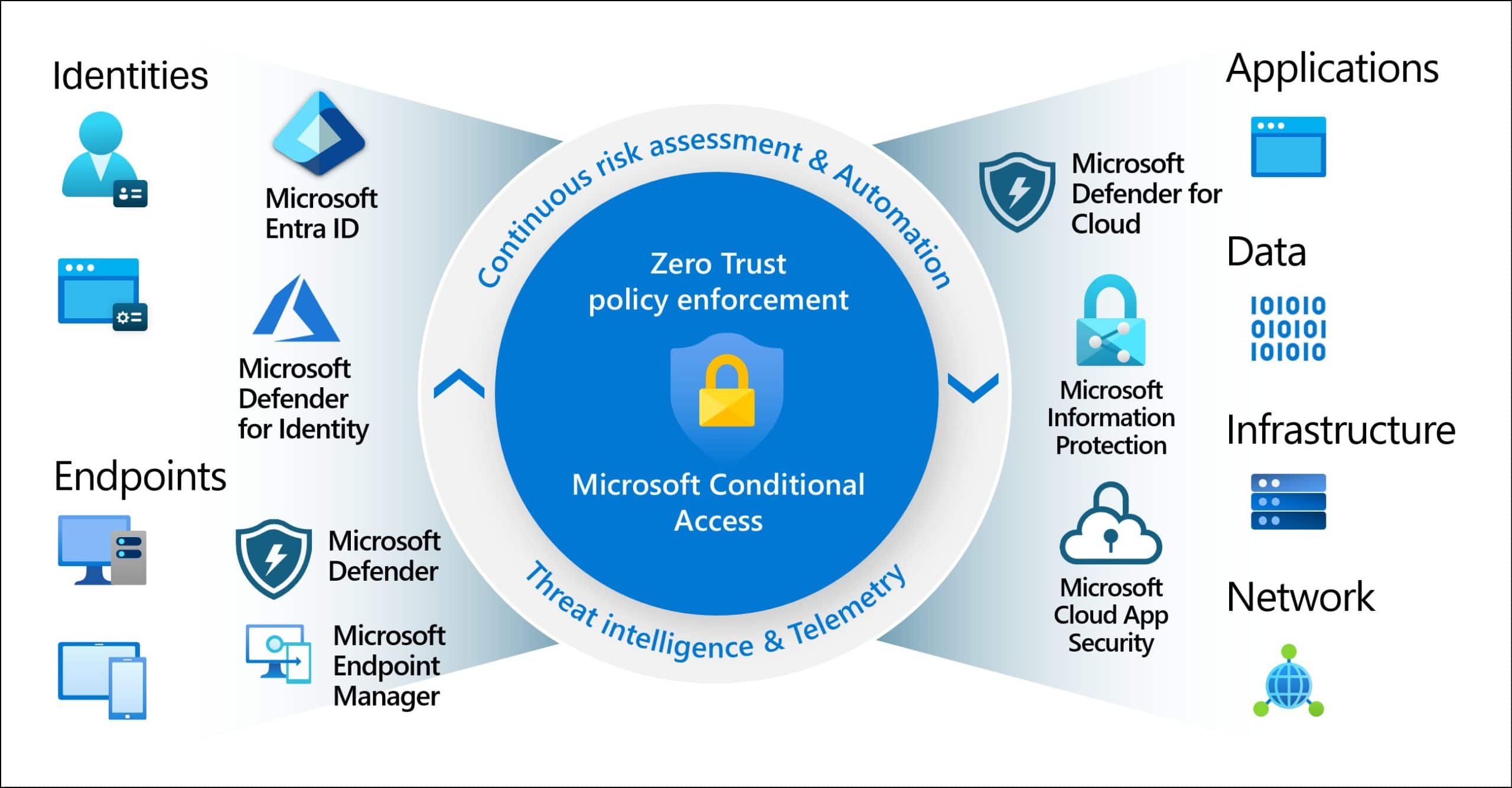
Step 4: Enable Self-Service Password Reset (SSPR)
- Goal: Allow users to reset their passwords without IT help.
- Actions:
- Navigate to SSPR: Azure portal > Azure Active Directory > Password reset.
- Select Users: Enable SSPR for ‘All users’.
- Authentication Methods: Allow users to choose between email and mobile phone verification. Example: Users can receive a code on their registered mobile or email to reset their password.
- Notify Users: Send out a tutorial email explaining how to set up their SSPR options through the Microsoft 365 user portal.
Step 5: Configure Azure AD Primary Authentication Method
- Goal: Enhance sign-in security.
- Actions:
- Choose Authentication Method: Decide on Microsoft Authenticator.
- Enable Microsoft Authenticator: Azure portal > Azure Active Directory > Security > Authentication methods > Microsoft Authenticator.
- Configure Settings: Activate and configure settings, guiding users through setup during the next login. Example: When John logs in next, he’ll be prompted to set up the Authenticator app.
- Inform Users: Create an easy-to-follow guide on setting up Multifactor Authentication Registration Policy and using Microsoft Authenticator, explaining its benefits like improved security and simpler sign-in.
Why Communication Square?
We've walked through some essential steps to tighten up your identity protection using Microsoft 365 Premium. By now, you should have a solid foundation in applying the principles of least privilege, managing emergency access, configuring access conditions, enabling self-service for password resets, and optimizing sign-in processes. These measures are crucial for protecting your organization against potential threats and ensuring your operations run smoothly and securely. Setting up Microsoft 365 identity protection correctly can greatly enhance your security posture.
However, if you're feeling unsure about handling these configurations on your own, or if you simply prefer to focus on your core business activities, help is just a click away. At Communication Square, we specialize in setting up Microsoft 365 identity protection to ensure your business's digital security is nothing short of excellent. Why not save time and gain peace of mind by letting experienced professionals handle your security needs?
Check out our services and see how we can help at Secure Microsoft Identity Protection. Don't hesitate to reach out—we're here to make sure your security setup is seamless and stress-free.
Now, let’s move on to some frequently asked questions that might give you further insights into securing your Microsoft 365 environment.
Frequently Asked Questions (FAQs)
Applying the principle of least privilege helps to minimize potential damage by ensuring that individuals have only the permissions they need to perform their job functions. This limits the risk of accidental or malicious misuse of permissions, reducing the potential security breaches and data leaks.
Create at least two cloud-only emergency access accounts with admin privileges and exclude them from Conditional Access policies that might otherwise lock them out. Secure these accounts with Multi-Factor Authentication (MFA) and use them strictly for emergencies to maintain their integrity.
Conditional Access policies allow you to define conditions under which users can access corporate resources. For example, you might require users to complete Multi-Factor Authentication when accessing sensitive data from outside the corporate network, thus enhancing security by adding an extra layer of verification.
Last Updated 7 months ago

