In today's digital world, understanding what is security and compliance is crucial for any organization aiming to protect its data and meet regulatory standards. They both help keep your business safe online, but they do it in different ways. In this blog, we will break down how each one works and why it is important to use both in today's digital world.
What is IT Security?
When we talk about security and compliance, IT Security is the first line of defense for your organization's digital assets. What is security and compliance in the context of IT?, IT Security serves as the first line of defense for safeguarding your company's digital assets. It aims to thwart unauthorized access, which can occur via cyber-attacks, data breaches, or leaks. The strategy is multi-faceted, targeting various risk areas like identity and access management, devices, emails, documents, applications, vulnerabilities, and networks.
Key IT Security measures commonly adopted include multi-factor authentication, data encryption, firewalls to block unauthorized access, and regular backups. Additional layers of protection come from antivirus software, data loss prevention policies, and ongoing employee training. Security audits and threat awareness also play pivotal roles in maintaining a secure environment.
By tailoring these security measures to the specific technological needs of your business, IT Security complements compliance efforts and ensures robust data protection.
Think of it like this: If your IT company provides cloud storage solutions, compliance would be like a quality assurance check that confirms you are storing client data securely, that you have the right encryption in place, and that you are following all laws and best practices for data protection. In this regard, understanding how specific services like Office 365 adhere to compliance standards such as HIPAA is crucial. Is Office 365 HIPAA Compliant? offers a deep dive into this specific aspect, providing you with detailed insights
How does IT Security Work?
In the context of security and compliance, it is crucial to understand that while both are aimed at safeguarding your business, they serve distinct roles. IT Security is all about putting defenses in place to protect your organization's data and systems. Here is how it works:
Security Measures | Description |
|---|---|
Firewalls | Enforces network traffic rules to allow or block data flow. |
Encryption | Protects data by making it unreadable without the correct decryption key. |
Antivirus Software | Protects against malware by detecting and removing malicious software. |
Enhances login security by requiring additional verification steps. | |
Updates & Patches | Maintains system security by fixing vulnerabilities and bugs. |
Data Backups | Safeguards against data loss from various incidents by keeping backup copies. |
In short, security puts up walls and barriers to keep your business safe, while compliance ensures you are following the rules that apply to your industry. Managed IT services San Francisco can help address both aspects effectively. Both are important, but they tackle different sides of protection.
What is Compliance?
Compliance means adhering to third-party requirements to ensure a business operates within set standards and rules. The objective is to assure clients, stakeholders, and regulatory bodies that your organization is diligently protecting data and respecting consumer rights. Understanding what is security and compliance involves recognizing how compliance frameworks like SOC 2, HIPAA, and ISO, standards play a role in validating your security practices.
Think of it like this: If your IT company provides cloud storage solutions, compliance would be like a quality assurance check that confirms you are storing client data securely, that you have the right encryption in place, and that you are following all laws and best practices for data protection. In this regard, understanding how specific services like Office 365 adhere to compliance standards such as HIPAA is crucial. Is Office 365 HIPAA Compliant? offers a deep dive into this specific aspect, providing you with detailed insights.
By having a solid grasp of information security compliance, you can robustly protect your IT company and meet or exceed industry standards.
With compliance it is not enough to merely claim that your business is safeguarding data and ensuring privacy. You must adhere to the stipulations of specific frameworks and then demonstrate this through third-party audits that validate your security measures. Making use of tools such as consent management platforms can further simplify compliance by ensuring proper tracking and documentation of user permissions and privacy preferences, helping your organization meet regulatory requirements efficiently.
This validation process can be extensive, requiring the rollout of security controls, internal policies, and operating procedures throughout your entire organization, along with supplying the necessary proof or evidence.
How does Compliance work?
Compliance works through a series of steps to ensure an organization meets legal, regulatory, and ethical standards. Here is how it works:
Product Name | Price |
|---|---|
Identify Regulations | Determine applicable laws, regulations, and standards for the industry and business operations. |
Risk Assessment | Evaluate the risks of non-compliance and prioritize them based on severity and likelihood. |
Develop Policies | Create or update internal policies and procedures to meet compliance requirements. |
Implement Controls | Put in place measures to enforce policies and mitigate identified risks. |
Monitoring | Regularly check compliance with policies and prepare reports for management and regulators. |
Audits | Conduct internal or external audits to assess compliance and the effectiveness of controls. |
Issue Resolution | Address non-compliance issues, take corrective actions, and prevent recurrence. |
What is Security and Compliance, Differences & Similarities Between Security and Compliance
While IT security and compliance share the goal of managing cyber risks and safeguarding sensitive data, their approach, driving forces, and scopes differ significantly. They are both crucial for organizations that rely on technology for data storage, processing, or transmission.
What sets them apart is their methods. Here is a quick rundown pf the differences and similarities between security and compliance:
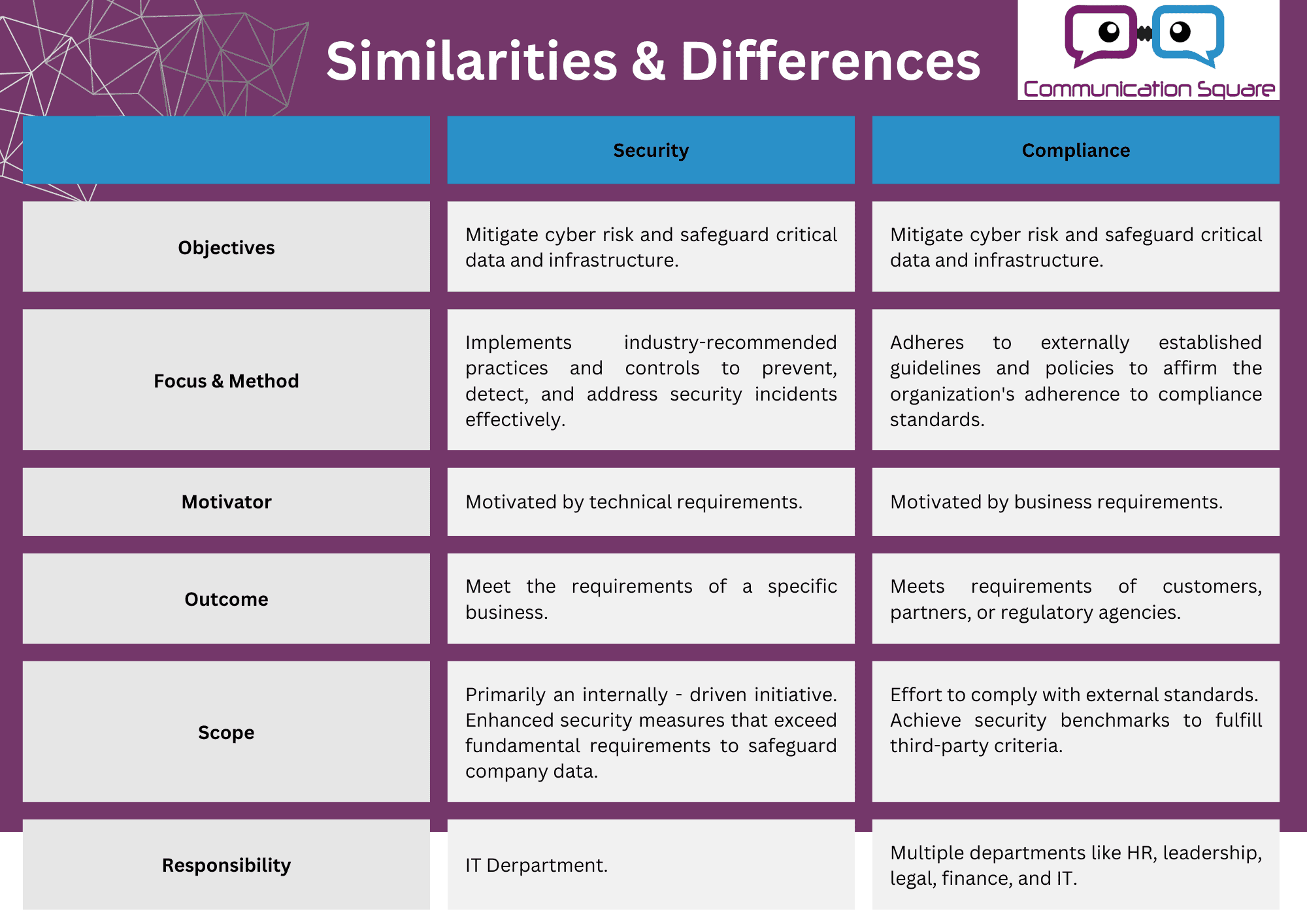
What is the importance of aligning security and compliance?
Navigating the tightrope of security and compliance is a bit like trying to find the perfect blend of spices for a recipe—it is essential to tailor it to your taste, or in this case, your business needs. Just ticking boxes on a compliance checklist is a good start, but it will not necessarily shield you from the storms of cyber threats. What is security and compliance if not the backbone of trust in the digital age? Think of it this way: having all the right gear does not automatically make you a seasoned mountaineer ready to conquer Everest. You need to train, plan, and adapt to the mountain's many unpredictable moods.
When it comes to your IT setup, it is not about wearing one-size-fits-all armor; it is about crafting a suit that fits your specific battle. It means understanding the unique risks your data and systems face, assembling a squad that clicks like a well-oiled machine, and honing a strategy that keeps getting better with every challenge you face.
By weaving security into the very fabric of your business strategy, you ensure that your IT is not just a silent guardian but also a strategic ally, pushing your business towards its goals. Security and compliance might seem like two dancers stepping on each other's toes, but once you understand their moves, they can waltz in harmony, protecting your data and fortifying the trust of those you do business with.
Pouring resources into security and compliance is more than a safety net; it is building a fortress that not only keeps the bad guys out but also serves as a bastion for your business's longevity. Whether it is shielding your data from the digital equivalent of a thunderstorm or meeting the stern gaze of regulatory bodies, security and compliance are the dynamic duo your organization should not overlook.
Conclusion
In conclusion, security and compliance are two sides of the same coin, yet they fulfill distinct roles within any organization. Security guards the fort, adapting to ever-changing cyber threats, while compliance ensures the fort is built to code, meeting all necessary regulations.
Striking a balance between security and compliance is less about choosing one over the other and more about recognizing how they complement each other to fortify your organization’s defenses. As you navigate this terrain, remember that checking off compliance boxes does not guarantee security, and robust security measures mean little if they do not align with compliance standards.
To ensure your business is fortified and compliant, book a strategy call with us today. Together, we will craft a security and compliance framework that safeguards and advances your operations. Start the conversation today—your path to robust security and compliance awaits.
Last Updated 3 months ago

