In today’s digital landscape, the threat of identity theft is a growing concern, especially for small and medium-sized businesses (SMBs) in the USA. As cybercriminals become more sophisticated, it's crucial for SMBs to have robust identity protection measures in place. For more information on how to implement identity protection, check out this comprehensive guide on Setting Up Microsoft 365 Identity Protection. How do I deal with identity theft is a question that every small business owner should ask themselves, as identity threats can lead to unauthorized access to sensitive data, financial losses, and significant reputational damage. Identity threats can lead to unauthorized access to sensitive data, financial losses, and significant reputational damage. Given that nearly 43% of cyberattacks target small businesses, and 60% of those businesses close within six months of a breach, it’s clear that taking proactive steps to protect your business is essential.
The focus of this guide is to provide you with actionable steps on how to get the best identity theft protection and deal with identity theft effectively. With the right strategies, tools, and support from experts like Communication Square LLC, you can protect your business and its valuable assets from these growing threats.
If you're curious about how identity protection works within the broader context of IT security, you might want to explore this comprehensive guide on SAML, which highlights authentication standards critical for protecting identity.
Understanding Identity Threats (ITDR)
Identity Threat Detection and Response (ITDR) is a critical aspect of cybersecurity that focuses on identifying and mitigating identity-based threats. These threats include various forms of unauthorized access, such as phishing, credential theft, and exploitation of security gaps. For SMBs, the consequences of identity threats can be particularly severe, as they often lack the extensive security infrastructure of larger organizations. Learning how do I deal with identity theft in this context is crucial to safeguarding your business.
For more tips on preventing unauthorized access, this guide on the Microsoft Authenticator App can help secure your systems with multi-factor authentication.
Common Types of Identity Threats
- Phishing: Cybercriminals use deceptive emails or websites to trick employees into providing sensitive information, such as login credentials.
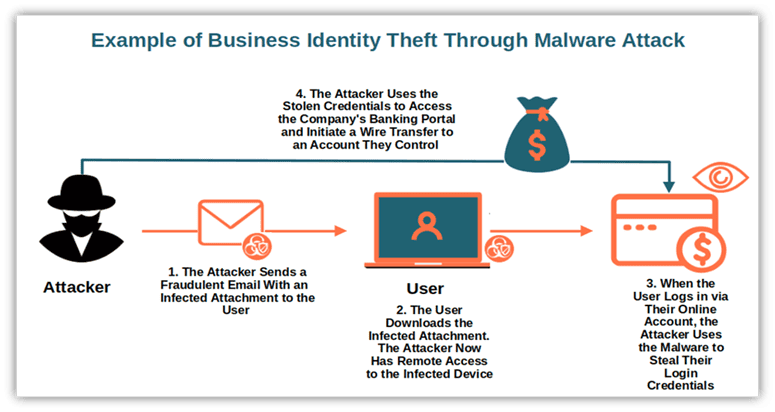
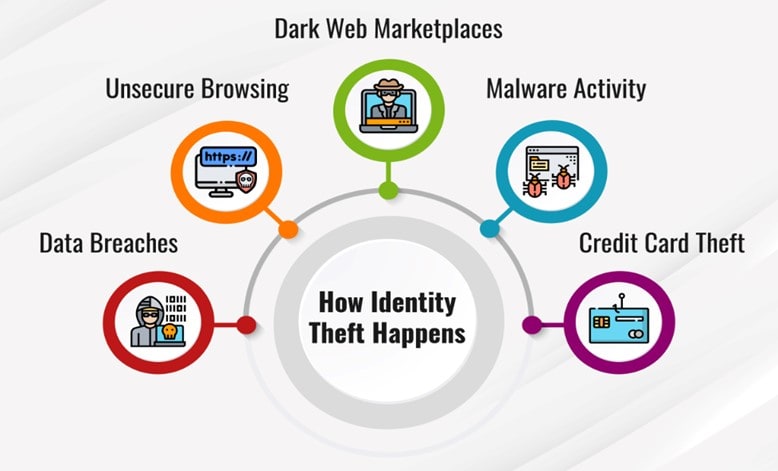
- Unauthorized Access: Malicious actors exploit security vulnerabilities to access sensitive data or systems without proper authorization.
These threats can cause significant harm, from financial losses to long-lasting damage to your business's reputation. According to recent reports, 77% of small businesses are increasing their cybersecurity budgets, reflecting the growing recognition of these risks and the importance of knowing how do I deal with identity theft.
How to Detect Identity Threats
Detecting identity threats early is crucial in minimizing their impact. Here are some key strategies and tools to help you stay ahead of potential breaches.
Proactive Monitoring
Continuous monitoring of identity-related activities within your organization is essential. This involves keeping an eye on login attempts, data access patterns, and other indicators that something might be amiss. By staying vigilant, you can catch suspicious behavior before it escalates into a full-blown breach. Understanding how do I deal with identity theft through proactive monitoring is a critical step in your defense strategy.
Key Indicators of Compromise (IoCs)
Look out for these signs that may indicate a compromise:
- Unusual Login Locations or Times: If users are logging in from unexpected locations or at odd hours, it could be a sign of unauthorized access.
- Multiple Failed Login Attempts: Repeated failed login attempts might indicate a brute-force attack.
- Sudden Access to Sensitive Data: If a user who typically doesn't access sensitive data suddenly does, it could be cause for concern.
Tools for Detection
Microsoft Entra ID
Microsoft Entra ID (formerly Azure Active Directory) is a powerful tool that helps monitor and detect suspicious activities across your organization. By leveraging Conditional Access Policies, you can set rules that block or limit access based on the risk level of a login attempt, significantly reducing the chances of a successful attack.
Microsoft Defender for Identity
This tool uses advanced machine learning to detect identity-based threats in real-time. It analyzes activities and alerts you to potential compromises, allowing you to take swift action. For more detailed information on how these tools can protect your business, check out this guide on Microsoft 365 for Enterprise Security.
How to Respond to Identity Threats
Once an identity threat has been detected, a quick and effective response is critical to minimizing damage. Here’s how you can respond to identity threats in your SMB.
Incident Response Plan
Having a well-defined incident response plan is essential. This plan should outline the steps to take when a threat is detected, ensuring a coordinated and effective response.
Immediate Steps
- Isolate the Threat: Immediately revoke access, lock accounts, and isolate affected systems to prevent the threat from spreading.
- Analyze the Breach: Assess the scope of the breach to determine what data was compromised and how it happened.
- Notification: Notify affected parties, including employees, customers, and, if necessary, regulatory bodies. Transparency is key to maintaining trust.
Using Microsoft Tools for Response
Microsoft Entra ID
In the event of a breach, Microsoft Entra ID allows you to quickly modify access controls, enforce new security measures, and monitor ongoing activities to prevent further unauthorized access. Learn more about Conditional Access Policies here.
Microsoft Defender for Identity
This tool can automate the response to identity threats, helping you contain the breach quickly. It provides detailed analysis of the threat, helping you understand how the breach occurred and what steps need to be taken to prevent future incidents. Check out Microsoft's official Defender for Identity page for more details on how this tool can enhance your cybersecurity.
For businesses looking to stay ahead of threats, we also recommend exploring Advanced Identity Protection, which provides insights into next-level tools for ensuring identity security.
Additionally, integrating theft insurance credit bureau monitoring can further protect your business by alerting you of fraudulent activities linked to your financial accounts and credit reports.
Case Studies and Real-World Application
Although specific case studies for these solutions are still being developed, Communication Square LLC has successfully provided identity protection solutions to various government and commercial customers in the USA. These real-world applications demonstrate the effectiveness of the tools and strategies discussed in this guide.
For example, Reynolds Logistics, a client of Communication Square, had this to say:
"I wanted my data to be as secure as possible regardless of where the data was stored or traveled. Communication Square offered a solution that completely configured our security management with ease." – Andrew Reynolds, Group CEO.
In addition to technology, clients also benefit from recommendations on the insurance credit bureau monitoring price, ensuring cost-effective solutions for comprehensive protection.
The Role of Communication Square LLC
Implementing these identity protection solutions effectively requires more than just technology—it requires expertise. That’s where Communication Square LLC comes in.
Expert Consultation
Communication Square consultants tailor Microsoft’s identity protection solutions to meet the unique needs of SMBs. They conduct thorough assessments of your current setup and recommend the best tools and practices to ensure comprehensive protection. They conduct thorough assessments of your current setup and recommend the best tools and practices to ensure comprehensive protection, including advice on the price of ID theft insurance credit monitoring solutions to provide an additional layer of defense.
Professional Setup and Ongoing Support
Cybersecurity isn’t a one-time task. It requires continuous monitoring and updates to stay ahead of emerging threats. Communication Square provides professional setup and ongoing support, ensuring that your systems remain secure as new challenges arise. If you’re ready to take the next step in securing your business, click here to learn more about Microsoft Identity Protection Solutions or schedule a meeting with a Communication Square consultant today.
If you’re ready to take the next step in securing your business, click here to learn more about Microsoft Identity Protection Solutions or schedule a meeting with a Communication Square consultant today.
Protecting your business from identity threats is not just about having the right tools—it's about having the right practices and partners in place. By following these strategies and leveraging Microsoft’s industry-leading solutions, you can ensure that your small business is well-protected against cyber threats. And with the expertise of Communication Square LLC, you’ll have peace of mind knowing that your identity protection measures are in the best possible hands. Don't leave your business vulnerable—act now and ensure you have the best rated ID theft protection on your side.
Last Updated 7 months ago

