Hello there! As a savvy business owner or an IT manager, you understand the importance of securing your company's devices. Whether you're using smartphones, tablets, or PCs, ensuring that each device is properly managed and secured is crucial to protecting your business data from various cyber threats. That’s where Setting up Microsoft 365 Endpoint Manager comes into play, offering powerful tools like Microsoft Endpoint Manager (Intune) to streamline this process.
In this guide, we'll walk you through how to set up endpoint enrollment in a way that’s not only straightforward but also tailored to small and midsize businesses. We’ll start with choosing the right mobility management approach and setting up device enrollment restrictions. Remember, while this guide aims to empower you to do it yourself, our team at Communication Square is always here to lend a hand if you need expert assistance along the way. Let’s get started and ensure your devices are set up for success!
Step 1: Choose Your Mobility Management Approach
- Goal: Select the appropriate management strategy for your devices based on ownership and usage.
- Actions:
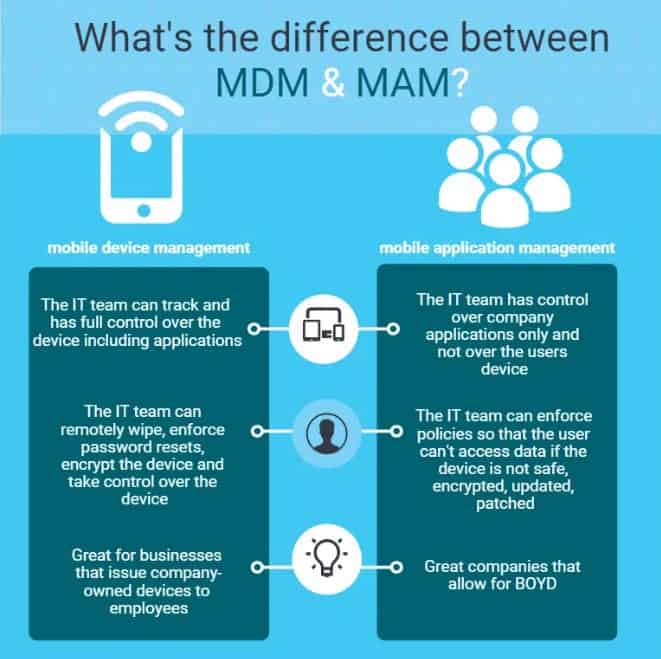
- For personally owned devices: Consider using Mobile App Management (MAM). MAM allows you to manage and secure corporate data within apps without taking control of the entire device, which is ideal for personal devices used for work purposes.
- For company-owned devices: It’s advisable to enroll these devices in Mobile Device Management (MDM). This approach gives you comprehensive control over the devices, allowing you to enforce security policies, perform remote actions, and manage configurations across all company-owned devices. For more insights into securing devices, check out this guide on Microsoft Authenticator App
- Helpful Insight: MAM is best for scenarios where user privacy is a priority, while MDM is suitable for situations where the company needs full control over the devices and the data on them. Make sure to align your choice with your company’s data security policies and compliance requirements. For more details, check out our guide on personal vs corporate devices, especially when using Microsoft 365 Office for iOS.
Step 2: Configure Device Enrollment Restrictions
- Goal: Define which devices are allowed to be enrolled in your management system and under what conditions.
- Actions:
- Set Platform Restrictions: Decide which types of devices (iOS, Android, macOS, Windows) your organization will support and configure the necessary settings in Microsoft Intune Admin Center to either allow or block enrollment based on these decisions.
- Block Personal Device Enrollment: For environments using MAM, it’s crucial to prevent personal devices from being enrolled in MDM. This can be configured to ensure that personal devices only receive app-level management, which protects both user privacy and corporate data.
- Guidance: Navigate to the Endpoint Manager admin center, and under “Devices” go to “Enrollment restrictions” to set up these controls. You can create different restriction profiles for different groups or scenarios within your organization.
Let’s move on to the second part of our guide on Setting up Microsoft 365 Endpoint Manager. This section will cover deploying app protection policies, preparing device enrollment prerequisites, and establishing compliance policies. By following these steps, you'll enhance the security of your business’s mobile devices and ensure that your company data remains protected.
Do you know? 43% of breaches take place at small business
Go Passwordless! The future is here for your Microsoft account, and it no longer requires a password! No more worrying about a breach happening to your business. This Free Inforgraphic will list everything that is potentially at risk and how to protect it.
Step 3: Deploy App Protection Policies (MAM)
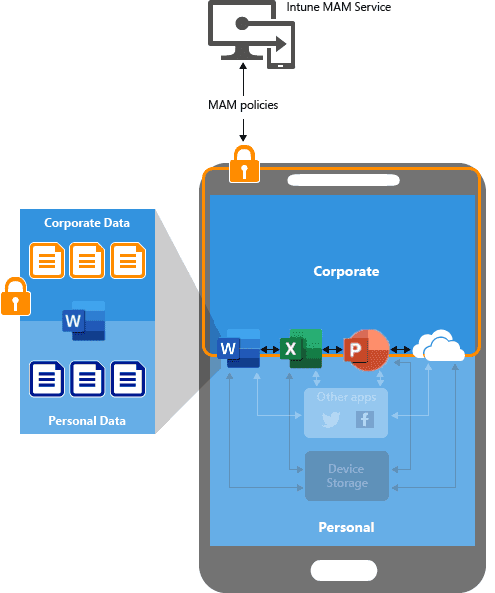
- Goal: Protect corporate data on mobile devices without enrolling the device itself.
- Actions:
- Create App Protection Policies: In Microsoft Endpoint Manager (Intune), create policies specifically for iOS/iPadOS and Android devices. These policies will help you manage and secure company data within apps effectively.
- Policy Settings: Implement settings such as requiring a PIN or biometric authentication to access Microsoft 365 Apps like Outlook. You can also restrict data transfer to only those apps that are managed by your company, preventing data from being saved to personal storage spaces like local device storage or non-corporate cloud services.
- Example Configuration: Configure policies to:
- Block data backup to iCloud (for iOS) or Google Cloud (for Android).
- Allow data transfer only to managed apps.
- Prevent the saving of copies of corporate data to unmanaged destinations.
- Resource Tip: You can find detailed guidance on creating and deploying these policies in the Microsoft Endpoint Manager documentation. You can also enhance your device management policies by implementing best practices for securing identities with Conditional Access.
Step 4: Configure Device Enrollment Prerequisites
- Goal: Ensure that all necessary conditions and tools are ready before starting the device enrollment process.
- Actions:
- Pre-Enrollment Steps: Depending on the device types your organization uses, you may need to:
- Obtain an Apple MDM Push certificate for iOS devices.
- Connect your Google Play account for managing Android devices.
- Set up Windows enrollment by configuring automatic enrollment in Endpoint Manager.
- Checklist: Make sure each platform's specific prerequisites are met to avoid any hiccups during the enrollment process.
- Guidance: Microsoft Configuration Manager provides a comprehensive setup guide for each platform, which you can follow to ensure all necessary steps are completed for device enrollment. For a detailed comparison of different management solutions, check out this article on Intune vs SCCM (System Center Configuration Manager)
Step 5: Create and Deploy Compliance Policies
- Goal: Establish baseline security standards that all devices must meet to access corporate resources.
- Actions:
- Develop Compliance Policies: In Microsoft Endpoint Manager, create compliance policies for each type of device your organization uses. These policies define the minimum security standards, such as encryption and device integrity checks.
- Example Settings for Windows Devices:
- Require BitLocker encryption.
- Ensure devices are secured with TPM chips.
- Mandate that firewalls, antivirus, and antispyware are active and up to date.
- Enforcement: Set up actions for noncompliance, such as blocking access to corporate resources or notifying IT administrators for manual intervention.
- Resource Tip: For further safeguarding your organization’s data, explore our Microsoft Data Protection Service, which provides comprehensive solutions for securing your critical business information, visit the Microsoft documentation on compliance policy settings.
These steps are crucial for maintaining control over how corporate data is accessed and stored on employee devices, ensuring that security is not compromised. By setting strong app protection policies and compliance standards, you're taking significant steps toward protecting your organization's data.
We're now heading into the final stretch of our guide on Setting up Microsoft 365 Endpoint Manager. In this last part, we'll discuss setting up device-based conditional access policies, the actual enrollment of devices, and wrap up with how you can continue to improve and secure your device management strategy.
Step 6: Enable Device-Based Conditional Access Policies with Microsoft Defender for Endpoint
- Goal: Ensure that only secure and compliant devices can access your business resources.
- Actions:
- Set Conditional Access Policies: In Microsoft Endpoint Manager, configure policies that control device access based on their compliance status and other security criteria.
- Key Policies to Implement:
- Require Multi-Factor Authentication (MFA): Set policies that require MFA when devices attempt to register with or join your Azure AD.
- Block Unknown or Unsupported Device Platforms: Prevent devices that do not meet your organization’s security standards from accessing business resources.
- Require Approved Apps or App Protection Policy for Access: Ensure that devices can only access corporate data through approved applications that are managed and secured by your policies.
- Resource Tip: You can find detailed guidance on creating and deploying these policies in the Microsoft Endpoint Manager documentation.
Step 7: Setup Device Enrollment Using Microsoft Intune
- Goal: Officially add devices to your organization’s management framework to ensure they are managed and secured.
- Actions:
- Enrollment Process: Guide users through the process of enrolling their devices, whether they are iOS, Android, macOS, Windows, or even Linux systems.
- Enrollment Guides: Provide clear, step-by-step instructions for each platform to ensure a smooth enrollment process. Utilize guides provided by Microsoft or create customized instructions specific to your organization’s setup.
- Example Enrollment Instructions: Direct users to the Microsoft Endpoint Manager admin center where they can start the enrollment process by adding their device.
- Resource Tip: Microsoft provides a comprehensive setup guide for each platform, which you can follow to ensure all necessary steps are completed for device enrollment.
Conclusion and Further Steps
Congratulations! You’ve now equipped yourself with the knowledge and tools to effectively enroll and manage devices in Microsoft 365 Business Premium. By following the steps outlined in this guide, you’ve laid a strong foundation for securing your organization's devices and the critical data they access.
However, the landscape of cybersecurity is always evolving, and staying ahead of potential threats requires continuous vigilance and adaptation. Keep your device management strategies up to date by regularly reviewing your settings, adapting to new security challenges, and educating your team on best practices.
However, the landscape of cybersecurity is always evolving, and staying ahead of potential threats requires continuous vigilance and adaptation. Keep your device management strategies up to date by regularly reviewing your settings, adapting to new security challenges, and reviewing your deployment strategy to ensure your company’s needs are met.
If at any point you find that you need additional support or would prefer to have experts manage your IT needs, Communication Square is here to help. We specialize in Microsoft solutions and can ensure that your device management is as seamless and secure as possible. Visit us at Microsoft Device Management to explore our services and find out how we can assist you in further securing your business. Let’s work together to keep your digital environment safe and productive!
With this guide and the right tools at your disposal, you're well on your way to mastering Setting up Microsoft 365 Endpoint Manager within Microsoft 365 Business Premium. Thank you for following along, and here’s to robust and streamlined device management in your business!
Here are some Frequently Asked Questions you might have:
Yes, Microsoft Endpoint Manager, which includes services like Intune, is available as part of the Microsoft 365 plans (formerly known as Office 365) that include enterprise mobility and security features. While it's not included in all Office 365 plans, it's available in higher-tier plans like Microsoft 365 Business Premium, Microsoft 365 E3, and E5. Be sure to check your specific plan to see if Microsoft Endpoint Manager is included.
Microsoft Endpoint Manager (MEM) doesn't require a traditional installation like software applications. Instead, you can access and configure it through the Microsoft Intune Admin Center within your Microsoft 365 account. To get started:
- Log in to the Microsoft Endpoint Manager Admin Center at endpoint.microsoft.com.
- Configure your settings, including device enrollment, compliance policies, and app protection policies.
- MEM integrates seamlessly with your Microsoft 365 environment, so there's no need for a separate installation process—everything is managed from the cloud.
If you're using Microsoft Configuration Manager in a hybrid setup, you can integrate it with Intune for co-management.
To configure Microsoft Endpoint Manager, follow these steps:
Access the Admin Center:
- Go to the Microsoft Endpoint Manager Admin Center at endpoint.microsoft.com and sign in with your Microsoft 365 credentials.
Set up Device Enrollment:
- Navigate to "Devices" and configure enrollment settings based on the type of devices (iOS, Android, Windows, macOS) your organization supports. You can set enrollment restrictions and platform-specific prerequisites.
Create Compliance Policies:
- Under "Devices," go to "Compliance Policies" and define the security standards that devices must meet to access company resources (e.g., encryption, password policies, antivirus requirements).
Configure App Protection Policies (MAM):
- In the "Apps" section, create app protection policies to safeguard corporate data on mobile devices. Set policies for data protection, requiring PINs, and restricting data transfer to managed apps like Microsoft 365 Apps.
Set Conditional Access Policies:
- Under "Security," configure conditional access policies to ensure that only compliant and secure devices can access corporate resources.
Once you've completed these steps, your environment will be ready to manage and secure devices efficiently. You can further customize settings based on your organization's needs.
Last Updated 3 months ago ago

